IF YOU DON’T WANT THE “FLUFF”, scan down to the next BOLD/CAPITAL heading for the “MEAT” of the post
Mea culpa, mea culpa. I have absolutely NO IDEA where the time goes, but it certainly flies. So sorry for being MIA, but the longer I didn’t write a post, the guiltier I got, then I got more embarrassed that I’d ‘abandoned’ you all. It was just a vicious circle. Finally, I decided that that was silly…just sit down and write SOMETHING, so here I am. If I haven’t written in a while, people will often say to me, “I think that coming up with the topics would be hard”. Actually, I have tons of topics…I lack the time to write the way that I want to write…to make the information sort of fun and accessible. I’ll try to do better…can’t promise, but I’ll try.
Next, people ask about my dear Uncle – 87-years-old and going strong. He’s well, thanks for your concern and thoughts. He currently has one laptop, one iPad, and two Android tablets. His home entertainment system (self-designed, self-put-togeether) rivals the best I’ve seen…it includes FOUR (yes, count ’em, four) Tivos, DVR’s and/or VCR’s, so that he NEVER has to watch TV live. I think he can record 6 shows on the Tivo, plus the assorted DVR/VCR devices for a total of 9 or 10 shows at one time. We always have plenty to watch when I visit.
Soooooooooooooo…on to the topic at hand.
HOW DO I CLEAN-UP/SPEED-UP MY LAPTOP
A few weeks ago, my Godkids were visiting (they’re actually young adults now), and my goddaughter, a professional photographer, had to edit some photos for a wedding (shameless promotion: She’s great! – check out her work – she knows how to make a photoshoot fun: Laurel Houston Photography), and her computer was ‘misbehaving’. We all know the syndrome…big project due…little time to do it…computer decides it won’t work efficiently.
Time for a little computer “spa” time. Yes, right in the middle of the big project, so that it was possible to actually get through the job without pulling out her hair or wasting valuable time with time-sucking crashes. Two FREE tools installed. A few cleanup processes run. Computer back to functioning ‘normally’. Project finished on time (another shameless plug…link to the wedding photos: Alex and Allison’s Wedding).
What did we do?
First, go to malwarebytes.org. Download and install the FREE utility (There’s a paid version that runs in the background all the time. The free version is ‘on demand’ meaning you have to run it manually). When you open up the newly installed Malwarebytes, you will see this screen:
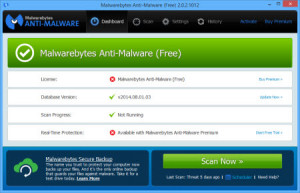
Click the large ‘Scan Now’ button. Malwarebytes is going to ‘do its thing’. What is it doing? It’s searching for any evil “stuff” that might have been dropped onto your computer without you knowing it. Some of the things are not malicious, some are evil. Whatever it is (and almost EVERY computer gets “stuff” if it’s connected to the internet), it tends to slow your computer down, or take resources that could be dedicated to your work.
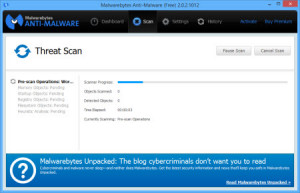
Go away for a little while…this could take a few minutes or an hour (or more) for the scan. Remember, “watched computer doesn’t clean”! When the scan is done, you want it to say this:
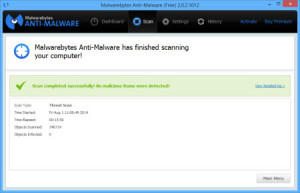
If instead, it looks like this:
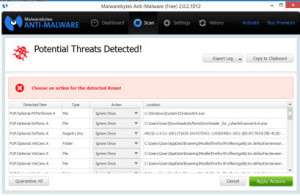
Click the ‘Quarantine All’ button ON THE LEFT SIDE. It will remove the offenders:
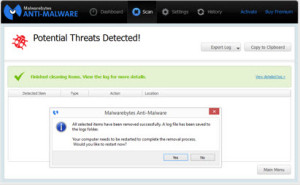
The resulting message will tell you that all is well now, and ask you to reboot your computer.
If the system finds issues, do the reboot after the quarantine, THEN RUN MALWAREBYTES AGAIN. Sometimes, everything isn’t caught the first time around. You want a ‘clean review’.
Now that you have any “cooties” cleared from your computer, it’s time to clean out your virtual closets, and throw away those shoes you haven’t worn in 5 years. No, I’m not making you go through your individual files and clean house there, but let your computer do a little housekeeping. Trust me, it does the heavy lifting, not you.
Go to piriform.com and download and install the FREE CCleaner utility (again, there’s a paid version, but the free one will do just fine, thank you). When you open it up, you will see this screen:
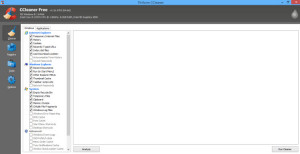
You can leave all of the default programs checked if you want, or manage what will be cleaned up. Note that there are two tabs (“Windows” and “Application”), so click both of them to see what will be tidied up.
Click the ‘Run Cleaner’ button on the lower-right side and let it “do it’s thing”. When it’s done, you’ll see this screen:
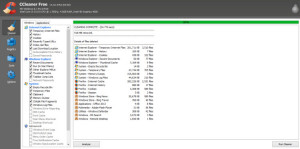
YOU’RE NOT DONE YET!
Next, click on the ‘Registry’ button on the left side:
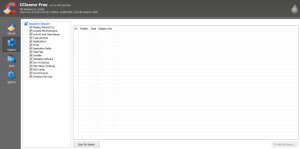
Click ‘Scan for Issues’.
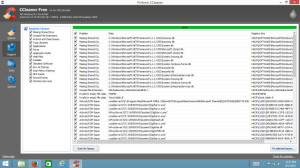
When it has finished, leave everything checked and click ‘Fix Selected Issues’. You will be asked if you want to backup your registry. SAY YES!!! You can leave the default location and name, but make sure that you DO BACKUP.
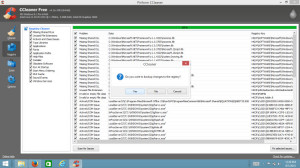
Once you have backed up your registry, click ‘Fix All Selected Issues’
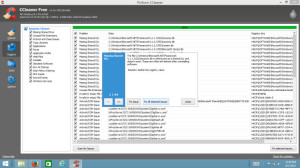
When it has finished, rerun your Registry Cleaner and repeat the steps above until the scan comes back empty. It can take a few passes. Sometimes you can’t see the boxes at the back of the closet until you’ve removed those at the front of the closet.
When it returns “clean”, reboot your computer…chances are that it starts up and moves a bit more easily.
Lastly, click on ‘Tools’ on the left side, then select ‘Startup’.
Click on the column heading ‘Enabled’ to sort by those processes which start when your computer starts and those that do not. Scroll down to the ‘Yes’ entries. Read the program name and published and decide if this program MUST START when your computer starts. The MORE ‘yes’ entries you have, the slower your computer will start. Remember, your programs will run even if they don’t start when your computer starts. For instance, I use Excel ALL THE TIME, but I do NOT have it start when my computer starts…it can open on its own when I need to use it.
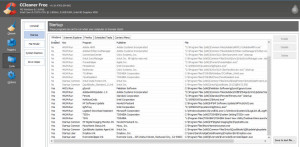
Do not simply select ‘no’ to enable at startup. SOME OF THE PROCESSES NEED TO RUN. For example, you want your anti-virus to run, you want your backup service to run, etc. Anything that you WANT to be in the task bar in the lower-right corner…leave all of those as ‘yes’ to enabled. If you don’t know what something is, saying ‘no’ could make the computer not boot correctly. If you don’t know what something does, Google “Does insert program name need to run at startup”, and read the advice.
Reboot and away you go.
Your computer should be sailing along more smoothly now!
Happy virtual cleaning!