Somehow, this seems appropriate during Halloween week…lots of warnings…lots of ‘be careful where you get your candy from’…Lots of ‘only trick-or-treat at houses you know’…that kind of thing.
Well, as we all know, the same sort of caution applies to entering ‘unknown places’ on your computer – be it opening emails from strangers (be careful), attachments from strangers (don’t do it), documents you find randomly surfing the web (be very, very cautious before doing it).
Enter the latest in the ‘Oh no, security on your computer isn’t all that’ string of potential threats that are out there.
Microsoft, yes Microsoft (it’s exploited most frequently because more machines are Microsoft than any other operating system), has discovered a POTENTIAL (this doesn’t mean you WILL or HAVE been compromised – just be aware) PowerPoint security flaw which could allow a stranger to totally take over your computer.
Thanks to TechCrunch for the head’s up! Click here for their excellent article by Greg Kumparak. For Microsoft’s security disclosure, click here (but it’s much duller than TechCrunch’s)
Here’s the low-down:
1. If you’re on ANY version of Windows, you’re probably affected
2. You have to open an infected PowerPoint (PPT or PPTX) presentation to have the vulnerability rear its ugly head.
3. The bug is part of the PowerPoint program which enables you to embed Excel files and the like inside of your presentations…that’s called OLE (‘Object Linking and Embedding’ for those of you who care about such things)…the bad guys do something to exploit a flaw in the security of such things and infect your computer along the way.
4. If the ‘bad thing’ runs, then the hackers can take over your computer as if they were the user who launched the PowerPoint presentation. What does this mean? Well, if you are like many of us with a laptop on which only YOU work, then you are an ADMINISTRATOR and can do ANYTHING on the computer…that means that the ‘bad guys’ will be an administrator too. If you’re on a Network, you’re not immune…it is just less likely that you’re an Administrator (and therefore, the bad guys have less access during an attack – they ‘captured’ a private instead of a general). If the evil ones invade, your Network Administrator will have to deal with the fallout.
5. One way to give you WARNING before just blithely opening random Powerpoint file is to ENABLE ‘User Account Control’ (available on Windows 7, Windows Server 2008 R2 and later). You can find this feature by searching for ‘User Account Control’. This is the screen:
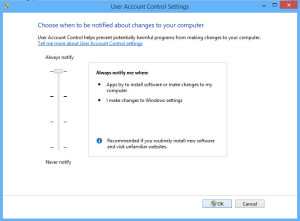
Make sure that your settings are set to ‘Always Notify’ (I’ll admit, mine were NOT because I find the warnings so annoying, but I changed them back)…THEN, THINK TWICE before saying ‘yes, open this document’…because an innocent PowerPoint presentation should NOT be changing your system.
6. If you maintain your own system, then go to this Windows link and install the ‘FixIt’ patch…it will fix 15 of the 18 possible combinations of Office and supported Windows environments.
As always, people, be ALERT. We tell our kids to be alert on Halloween, but we need to be alert on our computers ALL THE TIME. If you don’t remember asking someone for a particular PowerPoint presentation, if you don’t know the person who wrote it, if you found a presentation on the web, if you don’t know the author/sender then DO NOT open that Presentation. STOP. Ask the person who sent it to you (if you know them) if they really DID send it to you. A minute of double-checking can save you HOURS of heartache…just ask all the people who have been sucked into the Windows scam or electric company charades or opened infected PDF’s.